Your How does rsa signing work images are available in this site. How does rsa signing work are a topic that is being searched for and liked by netizens today. You can Find and Download the How does rsa signing work files here. Get all royalty-free images.
If you’re looking for how does rsa signing work pictures information related to the how does rsa signing work keyword, you have visit the ideal blog. Our site frequently provides you with hints for viewing the maximum quality video and image content, please kindly search and find more enlightening video content and graphics that fit your interests.
How Does Rsa Signing Work. One of these is digital signing for code and certificates. Each RSA SecurID authenticator has a unique symmetric key that is combined with a proven algorithm to generate a new one-time password OTP every 60 seconds. RSA algorithm is an asymmetric cryptography algorithm. Certificates can be used to verify who a public key belongs to by signing it with the private key of the key pair owner.
 Pin On Security From pinterest.com
Pin On Security From pinterest.com
Public Key and Private Key. Asymmetric actually means that it works on two different keys ie. The prime numbers are kept secret. Certificates can be used to verify who a public key belongs to by signing it with the private key of the key pair owner. Code signing is also done with the RSA. These keys generate a 6-digit numeric token which is set to expire However Ive always wondered how these work.
How does RSA digital signature work.
As the name describes that the Public Key is given to everyone and the Private key is kept private. The new point on the curve is very difficult to find even with the. A USB dongle or software a soft token which is assigned to a computer user and which generates an authentication code at fixed intervals usually 60 seconds using a built-in clock and the cards factory-encoded random key known as the seed. Each RSA SecurID authenticator has a unique symmetric key that is combined with a proven algorithm to generate a new one-time password OTP every 60 seconds. These keys generate a 6-digit numeric token which is set to expire However Ive always wondered how these work. More frequently it is used to encrypt and pass around symmetric keys which can actually deal with encryption at a faster speed.
 Source: in.pinterest.com
Source: in.pinterest.com
Patented technology synchronizes each authenticator with the security server ensuring a high level of security. The process of digital signing requires that the. Runtime system log and administrative activity at some point todays log data will be purged from the internal database at which time it will no longer be reflected in reports and written to archive files typically digitally signed. Certificates can be used to verify who a public key belongs to by signing it with the private key of the key pair owner. As previously described RSA encryption has a number of different tasks that it is used for.
 Source: in.pinterest.com
Source: in.pinterest.com
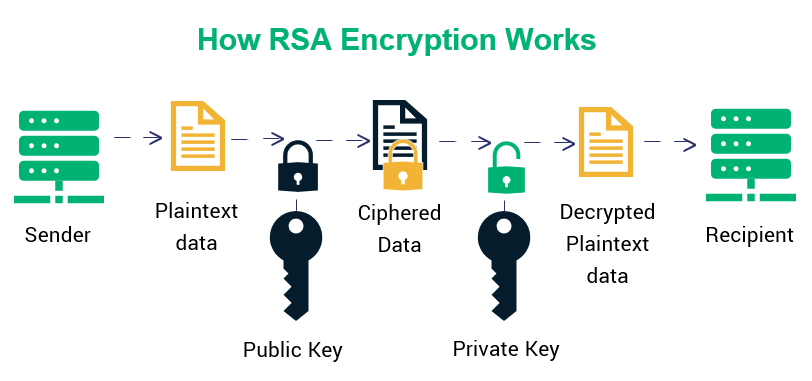
As RSA describes it. The signature can then be verified by applying the corresponding public key to the message and the signature through the verification process providing either a valid or invalid result. The new point on the curve is very difficult to find even with the. RSA encryption is often used in combination with other encryption schemes or for digital signatures which can prove the authenticity and integrity of a message. Public Key and Private Key.
 Source: security.stackexchange.com
Source: security.stackexchange.com
The RSA SecurID authentication mechanism consists of a token either hardware eg. As previously described RSA encryption has a number of different tasks that it is used for. Asymmetric actually means that it works on two different keys ie. Certificates can be used to verify who a public key belongs to by signing it with the private key of the key pair owner. What Is the RSA Algorithm.
 Source: pinterest.com
Source: pinterest.com
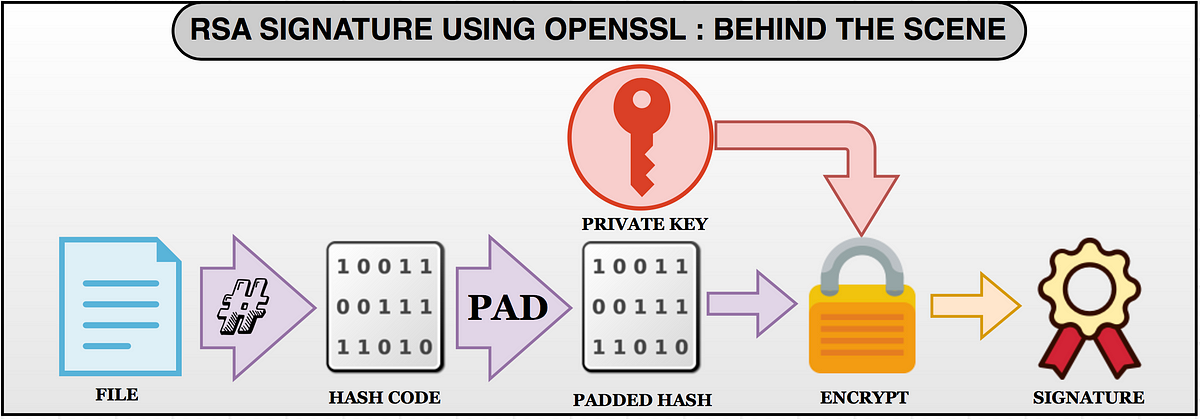
C m d mod n which enables the receiver to verify a message by decrypting it with public key e and comparing the result to unencrypted. On the right-hand side there is a dot not shown on the picture which blinks once per second and on the left there is a stack of six vertically-stacked horizontal bars each of which disappears once every ten seconds. The process of digital signing requires that the. One of these is digital signing for code and certificates. Complete answer to this is here.
 Source: medium.com
Source: medium.com
What is the process of digital signature. Asymmetric actually means that it works on two different keys ie. Their paper was first published in 1977 and the algorithm uses logarithmic functions to keep the working complex enough to withstand brute force and streamlined enough to be fast post-deployment. In unencrypted communication between a and b rsa signatures without utilizing hash functions are simply the message m encrypted with senders private key d not e as in usual encrypted communication. Based on archive settings for the three types of data.
 Source: pinterest.com
Source: pinterest.com
An RSA user creates and publishes a public key based on two large prime numbers along with an auxiliary value. One of these is digital signing for code and certificates. Their paper was first published in 1977 and the algorithm uses logarithmic functions to keep the working complex enough to withstand brute force and streamlined enough to be fast post-deployment. Both the public and private keys will encrypt a message in the RSA cryptography algorithm and a message is decrypted with the other key used to encrypt a message. These archive logs are only written to the primary or written to a remote Windows or.
 Source: pinterest.com
Source: pinterest.com
These archive logs are only written to the primary or written to a remote Windows or. The way ECDSA works is an elliptic curve is that an elliptic curve is analyzed and a point on the curve is selected. Each RSA SecurID authenticator has a unique symmetric key that is combined with a proven algorithm to generate a new one-time password OTP every 60 seconds. As the name describes that the Public Key is given to everyone and the Private key is kept private. More frequently it is used to encrypt and pass around symmetric keys which can actually deal with encryption at a faster speed.
 Source: in.pinterest.com
Source: in.pinterest.com
The RSA SecurID authentication mechanism consists of a token either hardware eg. The RSA SecurID authentication mechanism consists of a token either hardware eg. A USB dongle or software a soft token which is assigned to a computer user and which generates an authentication code at fixed intervals usually 60 seconds using a built-in clock and the cards factory-encoded random key known as the seed. That point is multiplied by another number thus creating a new point on the curve. This attribute makes RSA the most common asymmetric algorithm in use as it provides a way to ensure that electronic messages and data storage are kept secret complete and accurate.
 Source: pinterest.com
Source: pinterest.com
The RSA algorithm is a public-key signature algorithm developed by Ron Rivest Adi Shamir and Leonard Adleman. Complete answer to this is here. What Is the RSA Algorithm. The prime numbers are kept secret. The process of digital signing requires that the.
 Source: pinterest.com
Source: pinterest.com
Complete answer to this is here. This authenticates the key pair owner as a trusted source of information. Once activated the token is linked with the software VPN or server. What Is the RSA Algorithm. How does RSA digital signature work.
 Source: in.pinterest.com
Source: in.pinterest.com
Their paper was first published in 1977 and the algorithm uses logarithmic functions to keep the working complex enough to withstand brute force and streamlined enough to be fast post-deployment. Once activated the token is linked with the software VPN or server. Each RSA SecurID authenticator has a unique symmetric key that is combined with a proven algorithm to generate a new one-time password OTP every 60 seconds. The process of digital signing requires that the. What Is the RSA Algorithm.
 Source: crypto.stackexchange.com
Source: crypto.stackexchange.com
What is the process of digital signature. What Is the RSA Algorithm. How does RSA digital signature work. RSA Signatures The RSA public-key cryptosystem provides a digital signature scheme sign verify based on the math of the modular exponentiations and discrete logarithms and the computational difficulty of the RSA problem and its related integer factorization problem. The way ECDSA works is an elliptic curve is that an elliptic curve is analyzed and a point on the curve is selected.
 Source: co.pinterest.com
Source: co.pinterest.com
A USB dongle or software a soft token which is assigned to a computer user and which generates an authentication code at fixed intervals usually 60 seconds using a built-in clock and the cards factory-encoded random key known as the seed. Runtime system log and administrative activity at some point todays log data will be purged from the internal database at which time it will no longer be reflected in reports and written to archive files typically digitally signed. The RSA algorithm was published in the 70s by Ron Rivest Adi Shamir and Leonard Adleman hence RSA. As the name describes that the Public Key is given to everyone and the Private key is kept private. Based on archive settings for the three types of data.
 Source: pinterest.com
Source: pinterest.com
A USB dongle or software a soft token which is assigned to a computer user and which generates an authentication code at fixed intervals usually 60 seconds using a built-in clock and the cards factory-encoded random key known as the seed. What is the process of digital signature. Certificates can be used to verify who a public key belongs to by signing it with the private key of the key pair owner. The RSA digital signature scheme applies the senders private key to a message to generate a signature. Complete answer to this is here.
 Source: sectigostore.com
Source: sectigostore.com
The prime numbers are kept secret. What Is the RSA Algorithm. The RSA SecurID authentication mechanism consists of a token either hardware eg. This authenticates the key pair owner as a trusted source of information. Once activated the token is linked with the software VPN or server.
 Source: pinterest.com
Source: pinterest.com
The process of digital signing requires that the. A USB dongle or software a soft token which is assigned to a computer user and which generates an authentication code at fixed intervals usually 60 seconds using a built-in clock and the cards factory-encoded random key known as the seed. On the right-hand side there is a dot not shown on the picture which blinks once per second and on the left there is a stack of six vertically-stacked horizontal bars each of which disappears once every ten seconds. Their paper was first published in 1977 and the algorithm uses logarithmic functions to keep the working complex enough to withstand brute force and streamlined enough to be fast post-deployment. In unencrypted communication between a and b rsa signatures without utilizing hash functions are simply the message m encrypted with senders private key d not e as in usual encrypted communication.
 Source: pinterest.com
Source: pinterest.com
Code signing is also done with the RSA. RSA is an asymmetric system which means that a key pair will be generated a public key and a private key. RSA Signatures The RSA public-key cryptosystem provides a digital signature scheme sign verify based on the math of the modular exponentiations and discrete logarithms and the computational difficulty of the RSA problem and its related integer factorization problem. Once activated the token is linked with the software VPN or server. Patented technology synchronizes each authenticator with the security server ensuring a high level of security.
 Source: pinterest.com
Source: pinterest.com
More frequently it is used to encrypt and pass around symmetric keys which can actually deal with encryption at a faster speed. The RSA sign verify algorithm works as described below. Once activated the token is linked with the software VPN or server. This authenticates the key pair owner as a trusted source of information. RSA encryption is often used in combination with other encryption schemes or for digital signatures which can prove the authenticity and integrity of a message.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how does rsa signing work by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






